Security in Crypto, Hardware Wallets and Pseudonymity - Part 4/7
Part 4 discusses Software Wallets, their vulnerability to poor device security/user habits; harden devices with antivirus, anti-malware, VPN, Ad-Block
Part 4 discusses Software Wallets and how they are made vulnerable by poor device security and the user’s habits. We discuss how to harden devices using antivirus, anti-malware, VPN and Ad-Block; and the inevitable need to use Hardware Wallets to protect against 0-day attacks.
Software Wallets:
In Part 2, we discussed how a seed phrase allows your wallet to regenerate your “private key” and allows you to spend the assets in your wallet. In a Software Wallet, this private key lives on the same disk/memory as the wallet application. If the device such as the laptop or a mobile phone, on which the Software wallet is always connected to the internet, it is also termed as a Hot Wallet.
Some examples of Software Wallets on leading blockchains: Ethereum: MetaMask (as browser extensions + mobile), Trust Wallet (mainly mobile) Cardano: Nami (as browser extensions), Yoroi (as browser extensions + mobile), Daedalus (desktop only) Solana: Phantom (as browser extensions + mobile)
We will focus on Ethereum and MetaMask for now. MetaMask as a browser addon can be added to leading browsers such as Mozilla, Chrome, Brave, and Edge. It is a Software wallet because the seed phrase is entered into the UI of the browser addon, and the private key lives on disk + memory in the Laptop or Desktop. The utility of the Software wallet that is also Hot (i.e. internet connected) is that it can be readily used to make transactions. And thus has a lot of ease of use. The seed phrase only needs to be entered once, and it is encrypted on device with a second password that needs to be entered each time the MetaMask addon needs to be used/unlocked.
But this ready usability and ease of use comes at the cost of security. Modern operating systems have way too many moving parts and therefore a lot of security vulnerabilities arise from the edge cases when this added complexity breaks down.
Vulnerability of holding significant crypto in Software Wallets:
Targeted scams involve hacking into your computer and taking control of your Software wallet, such as MetaMask. This is a risk if you own significant amounts of crypto: read as anything above $2000, or you happen to be the lucky owner of a Blue Chip NFT such as CryptoPunks, or one of the newer Blue-Chip contenders NFTs – Bored Ape Yacht Club (BAYC), Proof, Moonbirds, Doodles, MAYC, etc.
Hardening Device Security and Privacy:
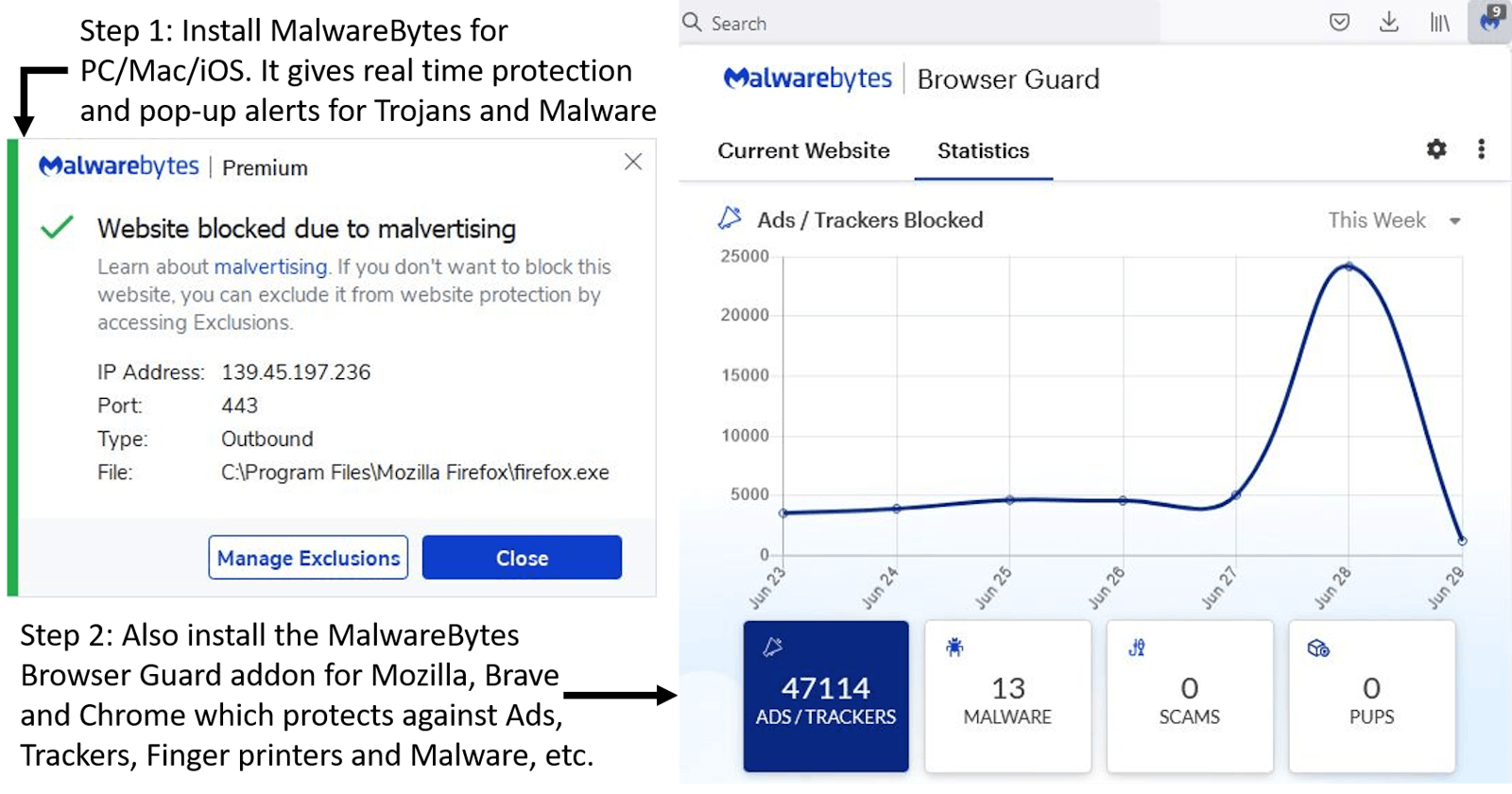
You need to obsessively protect your devices from viruses, malware and trojans - some of which can give complete remote control of your system to attackers. The only way to do it is by [a] using good paid antivirus software, such as McAfee[1] or Avast, [b] using anti-malware software such as MalwareBytes[2], that provides real time protection from browser page exploits and malware. Together, they should protect you from most types of keyloggers, trojans and web exploits. The capstone in self-protection software is using a VPN. It hides your identity and location from anyone trying to snoop, and thus makes it hard for you to be targeted using a meta analysis of the platforms and websites you visit. Again, paid and branded VPNs are preferred as compared to cheap, fly-by-night VPNs[3].
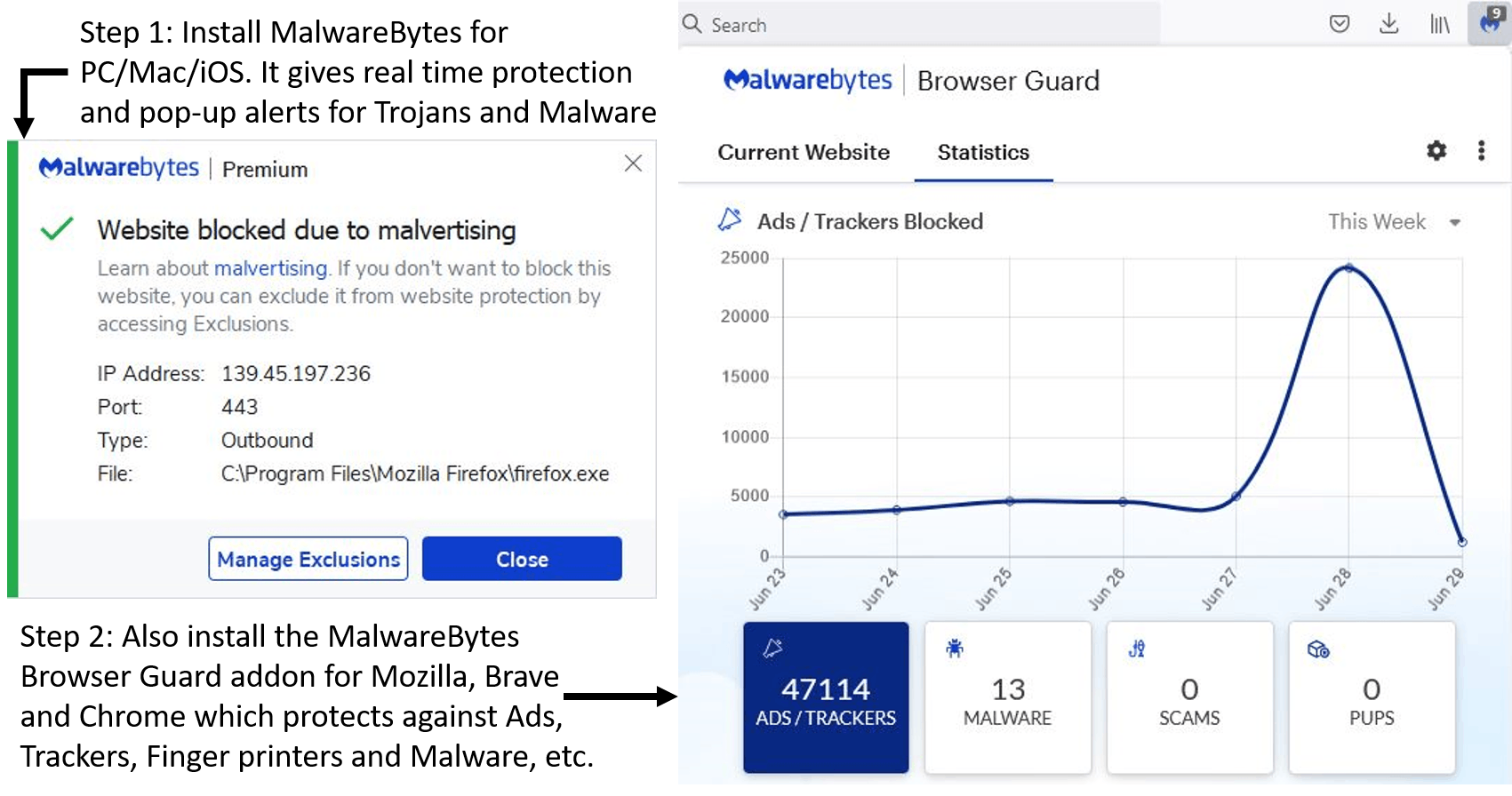
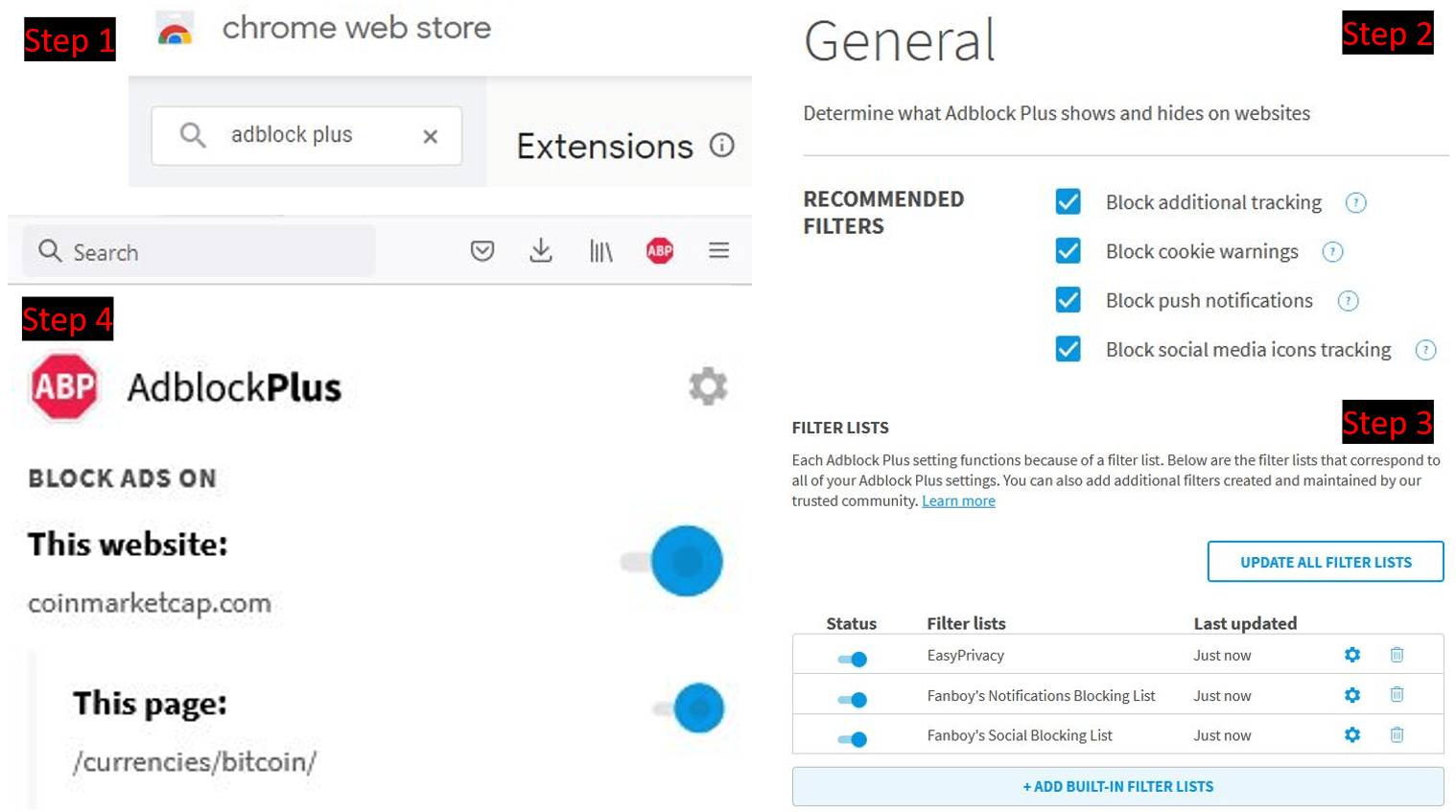
A final addition is to use Ad-blocking software such as Ad-Block Plus, which offers some protection against ads for fake/scam services[4].
0-day Attacks:
But even though you use anti-virus, anti-malware, VPNs and Ad-Block, you are still at risk. Since there are newer attacks each day, such as the multi-exploit 0-day Microsoft Word attack[5] exposed in May 2022 (I strongly urge you to understand the referenced Tweet thoroughly and implement their solutions to this exploit which includes not using or downloading Microsoft Word). These are not caught by the existing antivirus definitions. The only solution is a Crypto Wallet where private keys are inaccessible directly – these are called Hardware Wallets.
Vulnerability caused by user security habits:
The user’s security habits have a significant bearing on the vulnerability of the device. A user who installs cracked or warez software, or uses jailbreaking techniques to circumvent limits of major software and hardware, or visits porn websites, or installs unvetted browser addons[6] has a significantly higher risk of having their device affected with a virus, trojan or keylogger.
Over optimism against hacks leads to ruin:
If your crypto portfolio is anywhere above $2000, you need to invest in buying a Ledger Nano X and learning to use it appropriately. Procrastinating on this important step, and taking an over confident/over optimistic approach to your crypto, and thus continuing to hold it in a Software Wallet, exposes you to significant on-going risk of losing all your crypto. There are countless horror stories on Twitter, where people have lost $2-5M worth of tokens, because they were using MetaMask and not a Hardware Wallet[7]. A related hack is the use of Screensaver (*.scr) files with renamed extensions to pdf/jpg/etc., sent to desktops as demo art via DMs and emails, under the guise of commissioning artists, etc[8-14]. This scam might also take the form of sending investment portfolios to VCs, or employment contracts to crypto developers - so basically don’t download any unknown files from strangers on a computer you use for crypto wallets or exchanges.
References:
- Waugh, R. (2022). The best antivirus software of 2022, tried and tested to keep your family’s devices protected. The Telegraph. [online] 14 Feb. Available at: telegraph.co.uk/recommended/tech/best-antiv.. [Accessed 29 Jun. 2022].
- Rubenking, N.J. (2021). Malwarebytes Premium. [online] PCMag Australia. Available at: au.pcmag.com/antivirus/3815/malwarebytes-pr.. [Accessed 29 Jun. 2022].
- Rubenking, N.J. and Eddy, M. (2022). The Best iPhone VPNs for 2022. [online] PCMag Australia. Available at: au.pcmag.com/vpn/48365/the-best-iphone-vpns [Accessed 29 Jun. 2022].
- Eddy, M. (2022). The Best Ad Blockers for 2022. [online] PCMag Australia. Available at: au.pcmag.com/security/93748/the-best-ad-blo.. [Accessed 29 Jun. 2022].
- Wallet Guard (2022). A severe 0-day vulnerability called #Follina has been exposed (since May 27th) in MS Word Documents. [online] Twitter. Available at: twitter.com/wallet_guard/status/15318484799.. [Accessed 29 Jun. 2022].
- Evuri, M. (2020). How Browser Extensions can Exploit User Activities for Malicious Operations - CloudSEK. [online] cloudsek.com. Available at: cloudsek.com/how-browser-extensions-can-exp.. [Accessed 29 Jun. 2022].
- 0xflim on Twitter (2021). twitter.com/0xflim/status/1459673602874249216. [online] Twitter. Available at: twitter.com/0xflim/status/1459673602874249216 [Accessed 29 Jun. 2022].
- Serpent on Twitter (2022). twitter.com/serpent/status/1540770171069276... [online] Twitter. Available at: twitter.com/Serpent/status/1540770171069276.. [Accessed 29 Jun. 2022].
- Fvckrender on Twitter (2021). twitter.com/fvckrender/status/1403471996017... [online] Twitter. Available at: twitter.com/fvckrender/status/1403471996017.. [Accessed 30 Jun. 2022].
- Dorland, J. van (2021). The .SCR Malware Hack Explained. [online] Julien’s Newsletter. Available at: julienvandorland.substack.com/p/the-scr-mal.. [Accessed 30 Jun. 2022].
- NftNir on Twitter (2022). twitter.com/nftnir/status/1541671263747592192. [online] Twitter. Available at: twitter.com/NftNir/status/1541671263747592192 [Accessed 29 Jun. 2022].
- HeisenbergSol on Twitter (2022). twitter.com/heisenbergsol/status/1528289657... [online] Twitter. Available at: twitter.com/HeisenbergSol/status/1528289657.. [Accessed 29 Jun. 2022].
- CGREND_Art on Twitter (2022). twitter.com/cgrend_art/status/1541378860444... [online] Twitter. Available at: twitter.com/CGREND_Art/status/1541378860444.. [Accessed 30 Jun. 2022].
- dmcxblue (David) (2020). SCR Files - Red Team Notes. [online] Gitbook.io. Available at: dmcxblue.gitbook.io/red-team-notes/initial-.. [Accessed 29 Jun. 2022].
The author holds a M.S. in Engineering from Columbia University, and has a decade of research and industry experience in software and hardware design. He has been researching crypto security since early 2021. He can be followed on Twitter: @MetaversityOne and also his Hashnode Blog: https://cryptosecurity.hashnode.dev/