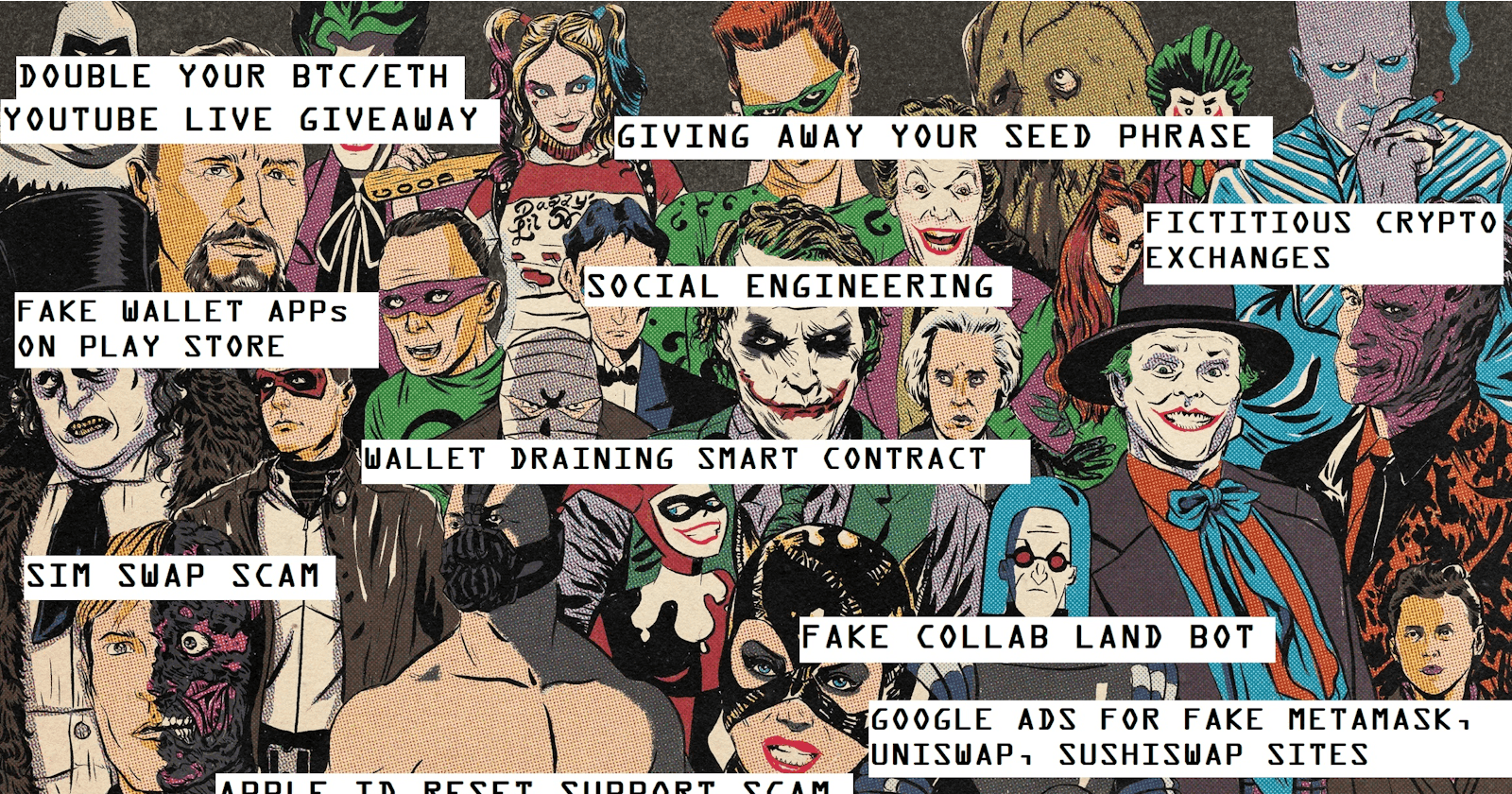
Security in Crypto, Hardware Wallets and Pseudonymity - Part 3/7
Part 3 discusses self-custody of crypto assets, along with all the rights and responsibilities self-custody imposes on the user.
Part 3 discusses self-custody of crypto assets, along with all the rights and responsibilities self-custody imposes on the user.
Crypto self-custody empowers you to be your own bank… But with great power comes great responsibility.
A meta theme I want to convey to those not aware of it: By using a crypto wallet, you are opting for 'Self-custody'. This saves you from all manner of frauds and mismanagement by a central party/middlemen - such as banks (think 2007 Subprime crisis [1]), centralized exchanges (think Mt. Gox hack [2] in 2013-14 and the dozens of exchanges hacked since then [3,4,5]), centralized crypto protocols and hedge funds and so on (Think of all the crypto bad news you have heard in the 2022 about over-leveraged funds like Celsius [6], 3ArrowsCapital [7], Voyager [7], etc).
User mistakes and scams in Crypto can be expensive: But in the same stroke, with Self-custody you are also responsible for your own actions – actions that cause you financial damage due to:
- Lack of knowledge (e.g. Impermanent Loss for Uniswap LPs exceeds fee earnings [8]), or
- Actions done by you when you were stressed/sleepy/tired and entered a wrong wallet address/fat fingered the value/made a sloppy mistake [9], or
- Interaction with a scam contract/scam website with your wallet, didn’t read what transaction/message you were signing (N.B.: it is possible to simply sign a gasless message and yet have your wallet drained, refer [10]) or
- GIVING AWAY YOUR SEED PHRASE in a confidence scam [11], or
- Falling for a Youtube/Twitter Crypto Giveaway scam with the face of Elon Musk/Vitalik Buterin/Charles Hoskinson, etc. [12] on it offering to double your BTC/ETH/ADA coins. There is not one legitimate ‘double your crypto coin’ scheme out there - all of them are scams. (N.B.: In 2020, 130 high profile Twitter accounts were hacked via social engineering and used to run a mass scale Bitcoin double your coins scam [13]), or
- Falling for the Apple ID Reset Support Scam, where a scammer tries to talk you into giving away your 6-digit Apple ID reset code [14] and the scammer proceeds to restore your Apple account on iOS along with your Metamask private keys (N.B.: This scam is also possible with Google Accounts). The solution is turn off cloud backup for the Metamask app on your iOS by going to Settings -> User Profile -> iCloud ->Manage Storage -> Backups -> Metamask [15], or
- Downloading a fake wallet application and entering your seed phrase to restore an existing wallet, only to have the wallet contents wiped clean. Happens mostly on Google Play Store [16,17,18], where a lot of fake wallet applications are allowed to fester. Always check the developer credentials before downloading an app. The most wicked trick are wallets which don’t even exist on that platform, e.g. Cardano Daedalus wallet is only for desktops, yet people fall for the fake Play Store versions and lose their coins [18]. Thus checking app ratings, downloads count, etc., are not enough to ensure the app is genuine - spend time on the official wallet developer website/Twitter account to understand what you are doing; don’t be in haste when it comes to wallets.
- Falling for the fake crypto exchange/fake high yield DeFi scheme, termed as the Pig Butchering Scam [19,20] - because victims are lured into parting with increasingly bigger sums of money. These may sometimes be preceded by a romance scam, but this is not always the case.
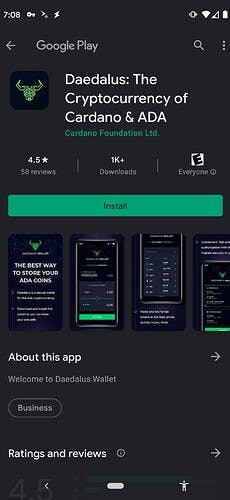 Fake Daedalus wallet on Google Play Store with 1000+ downloads [18]
Fake Daedalus wallet on Google Play Store with 1000+ downloads [18]
Another major threat is phishing. The security conscious exchanges utilize user defined anti-Phishing codewords to uniquely identify their emails as legitimate. But there are newer threats, such as placing 'Google Ads for fake sites’ on important pages like top of Google Search results page [21,22], etherscan.io [23,24], CoinGecko [23,24], etc. A distracted/lazy user will spot an ad from Binance, MetaMask, Uniswap, Sushi Swap, etc, click on it, quickly type their password/connect their wallet and perform a transaction on the web page that opens by clicking the Ad. But it might not be the real deal. Instead, you have just given away your login id and password, or signed a transaction from your Metamask on a fake website that drained your wallet [23,24], or worse gave away your seed phrase because you believed you had to “restore”, “verify” or “sync” your wallet [21,22].
 Image Credits [25]
Image Credits [25]
ALL THESE ACTIONS ARE IRREVERSIBLE AND NOT INSURED BY ANY MEANS. YOU ARE YOUR OWN BANK.
This is a very significant responsibility. Do not make major financial decisions in crypto, when you might be unsure about what you are doing, or tired/stressed/sleepy. Do not greed let you drop your guard, when you think you have to mint or stake or buy a token/NFT within the next 5 minutes. There is no financial instrument that has a 5 minute buy-in window. Even Bitcoin was below $100 for 4 years, and BAYC was below 1ETH for 3 months.
The number of long-term crypto investors I know, who have given away their seed phrase willingly by trusting a “helpful” looking stranger on Discord and Telegram is mind numbing. Many of them were in a rush to get a wallet connection working, and their tiredness/inattention cost them a lot. There are a dozen variations of the seed phrase scam. Almost always, the victim knowingly shares it with someone who has gained their confidence OR the victim enters their seed phrase into a phishing website when in a hurry and pressured to “verify their wallet” or “sync their wallet”, before they can receive an airdrop or some support. Almost universally, there is nothing called "syncing your wallet". The wallet lives on the blockchain, and the blockchain is syncing and reaching consensus by itself with every block. Verifying wallet ownership for Discord servers is a real task, and most likely happens with the Collab Land bot. You must ensure that you are not interacting with a fake bot and are on the correct website. Carefully read the message you sign, and ensure there is no transaction with token approvals being signed.
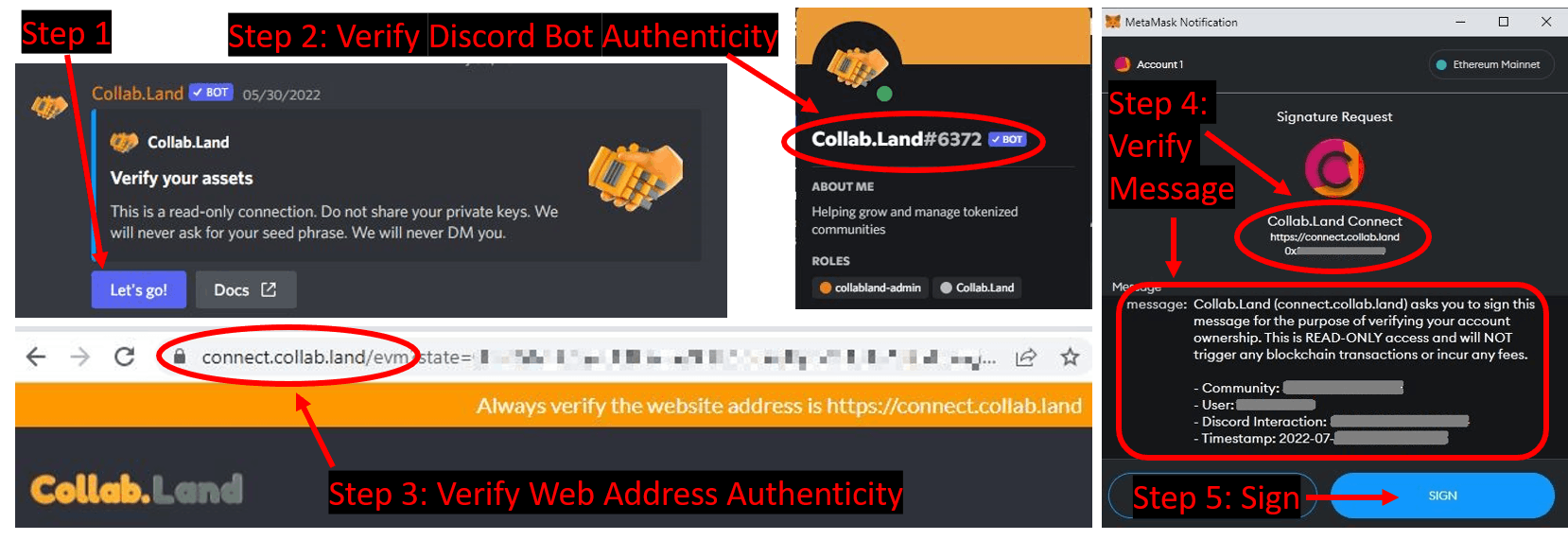
Some newer Discord servers utilize a service called ‘Vulcan Authentication’ Bot, that utilizes the Profile Bio attribute of Opensea wallet-based accounts: the user is allotted a short duration of time to change the Profile Bio to a custom string generated by the bot [26]. Since only wallet owners can make this change, successfully doing so in the allotted time proves wallet ownership. This ensures the wallet owner only needs to interact with OpenSea.io, which is a much more recognizable and distinguishable website than collab.land or other 3rd party websites.
References:
- Wikipedia Contributors (2019). Subprime mortgage crisis. [online] Wikipedia. Available at: en.wikipedia.org/wiki/Subprime_mortgage_cri.. [Accessed 27 Jun. 2022].
- Wikipedia Contributors (2022). Mt. Gox. [online] Available at: en.wikipedia.org/wiki/Mt._Gox#Bankruptcy [Accessed 27 Jun. 2022].
- WIRED Staff (2019). Hackers Stole $40 Million From Binance Cryptocurrency Exchange. [online] WIRED. Available at: wired.com/story/hack-binance-cryptocurrency.. [Accessed 3 Jul. 2022].
- Chainalysis Team (2020). The KuCoin Hack: What We Know So Far and How the Hackers are Using DeFi Protocols to Launder Stolen Funds. [online] Chainalysis. Available at: blog.chainalysis.com/reports/kucoin-hack-20.. [Accessed 3 Jul. 2022].
- Ramaswamy, A. (2022). 2FA compromise led to $34M Crypto.com hack. [online] TechCrunch. Available at: techcrunch.com/2022/01/20/2fa-compromise-le.. [Accessed 3 Jul. 2022].
- Knight, O. (2022). How Crypto Lender Celsius Overheated. [online] coindesk.com. Available at: coindesk.com/business/2022/06/16/how-crypto.. [Accessed 27 Jun. 2022].
- Malwa, S. (2022). Three Arrows Capital Confirms Heavy Losses From LUNA’s Collapse, Exploring Potential Options: Report. [online] coindesk.com. Available at: coindesk.com/business/2022/06/17/three-arro.. [Accessed 27 Jun. 2022].
- Newar, B. (2021). Half of Uniswap v3 liquidity providers are losing money: New research. [online] Cointelegraph. Available at: cointelegraph.com/news/half-of-uniswap-v3-l.. [Accessed 3 Jul. 2022].
- Boom, D.V. (2022). How a $300K Bored Ape Yacht Club NFT was accidentally sold for $3K. [online] CNET. Available at: cnet.com/culture/how-a-300k-bored-ape-yacht.. [Accessed 3 Jul. 2022].
- CT_IOE (2022). twitter.com/ct_ioe/status/1534658825843683328. [online] Twitter. Available at: twitter.com/ct_ioe/status/1534658825843683328 [Accessed 28 Jun. 2022].
- Dedenok, R. (2022). Cryptoscam giveaway: phishers go after seed phrases. [online] kaspersky.com. Available at: kaspersky.com/blog/cryptocurrency-giveaway-.. [Accessed 27 Jun. 2022].
- Kozhipatt, J. (2022). 5 Social Media Crypto Scams to Avoid. [online] coindesk.com. Available at: coindesk.com/learn/5-social-media-crypto-sc.. [Accessed 27 Jun. 2022].
- Wikipedia Contributors (2021). 2020 Twitter account hijacking. [online] Wikipedia. Available at: en.wikipedia.org/wiki/2020_Twitter_account_.. [Accessed 3 Jul. 2022].
- Haber, J. (2022). twitter.com/jasonhaber/status/1527255440580... [online] Twitter. Available at: twitter.com/jasonhaber/status/1527255440580.. [Accessed 28 Jun. 2022].
- Newbery, E. (2022). Do You Use MetaMask With an Apple Device? Your Account May Be at Risk. [online] The Motley Fool. Available at: fool.com/the-ascent/cryptocurrency/articles.. [Accessed 28 Jun. 2022].
- Alexandre, A. (2018). Four Fake Cryptocurrency Wallets Found on Google Play Store. [online] Cointelegraph. Available at: cointelegraph.com/news/four-fake-cryptocurr.. [Accessed 28 Jun. 2022].
- Simms, T. (2019). Fake Crypto Wallet App Imitating Trezor Found on Google Play Store. [online] Cointelegraph. Available at: cointelegraph.com/news/fake-crypto-wallet-a.. [Accessed 28 Jun. 2022].
- Alex, D. (2021). WARNING: A fake #Daedalus app is back on the Google Play Store. There is no mobile app for Daedalus. Anyone who uses this app will have their ADA stolen. [online] Cardano Forum. Available at: forum.cardano.org/t/warning-a-fake-daedalus.. [Accessed 3 Jul. 2022].
- Rojas, M. (2022). Hunting Fake Cryptocurrency Exchanges. [online] maltego.com. Available at: maltego.com/blog/hunting-fake-cryptocurrenc.. [Accessed 3 Jul. 2022].
- Farivar, C. (2022). ‘Pig Butchering’ Crypto Scam Victim To Get Money Back From Binance, Law Enforcement Says. [online] Forbes. Available at: forbes.com/sites/cyrusfarivar/2022/07/01/pi.. [Accessed 3 Jul. 2022].
- Barda, D., Zaikin, R. and Vanunu, O. (2021). CPR alerts crypto wallet users of massive search engine phishing campaign that has resulted in at least half a million dollars being stolen. [online] Check Point Research. Available at: research.checkpoint.com/2021/cpr-alerts-cry.. [Accessed 3 Jul. 2022].
- Ecency. (2021). Scammers Advertising on Google Ads Sushiswap. [online] Available at: ecency.com/history/@digitalworldyou/scammer.. [Accessed 3 Jul. 2022].
- Sarkar, A. (2022). Etherscan, CoinGecko warn against ongoing MetaMask phishing attacks. [online] Cointelegraph. Available at: cointelegraph.com/news/etherscan-coingecko-.. [Accessed 3 Jul. 2022].
- Lawler, R. (2022). Phishing attack pop-up targets MetaMask users visiting popular crypto sites. [online] The Verge. Available at: theverge.com/2022/5/13/23071786/etherscan-c.. [Accessed 3 Jul. 2022].
- Staff, T.R. (2022). The 25 Best Batman Villains, Ranked. [online] The Ringer. Available at: theringer.com/2022/3/2/22957043/batman-vill.. [Accessed 28 Jun. 2022].
- Vulcan (n.d.). Vulcan Authentication. [online] vulcanbot.io. Available at: vulcanbot.io [Accessed 14 Jul. 2022].
The author holds a M.S. in Engineering from Columbia University, and has a decade of research and industry experience in software and hardware design. He has been researching crypto security since early 2021. He can be followed on Twitter: @MetaversityOne and also his Hashnode Blog: https://cryptosecurity.hashnode.dev/