Security in Crypto, Hardware Wallets and Pseudonymity - Part 2/7
Part 2 discusses Asymmetric encryption, its application to Bitcoin, Public Keys, Private Keys, seed phrase and securing the seed phrase, etc.
**Part 2 discusses Asymmetric encryption, its application to Bitcoin (and cryptocurrencies in general), Public Keys, Private Keys (spending password), seed phrase, and securing your seed phrase without digitizing it. **
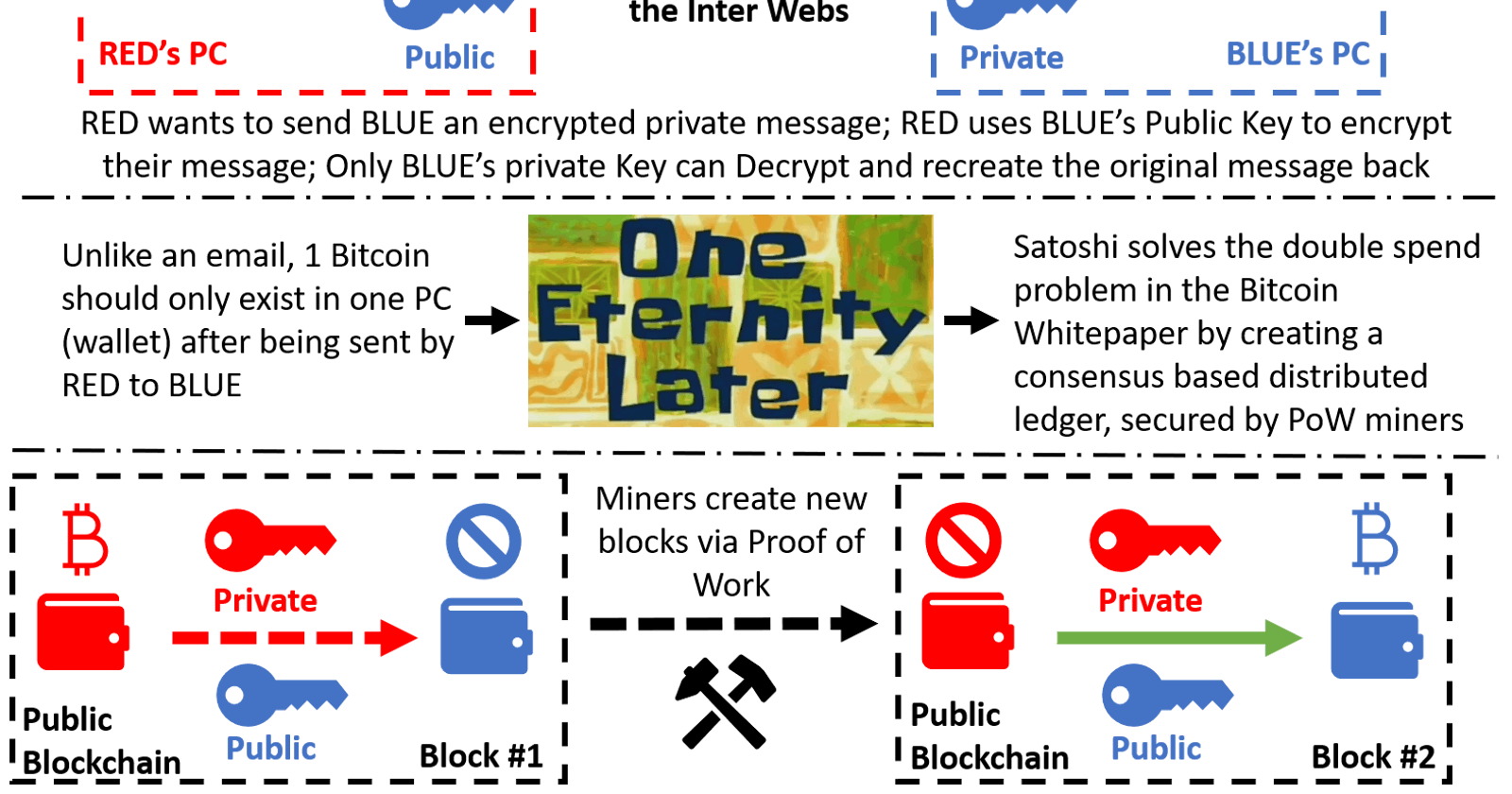
Asymmetric Encryption: Before we can discuss Public Key and Private Key (Spending Passwords) in crypto, we need to understand Public Key or Asymmetric Encryption [1,2]. Since this topic is beyond the scope of this primer, I will refer you to the contributors on Wikipedia: https://en.wikipedia.org/wiki/Public-key_cryptography
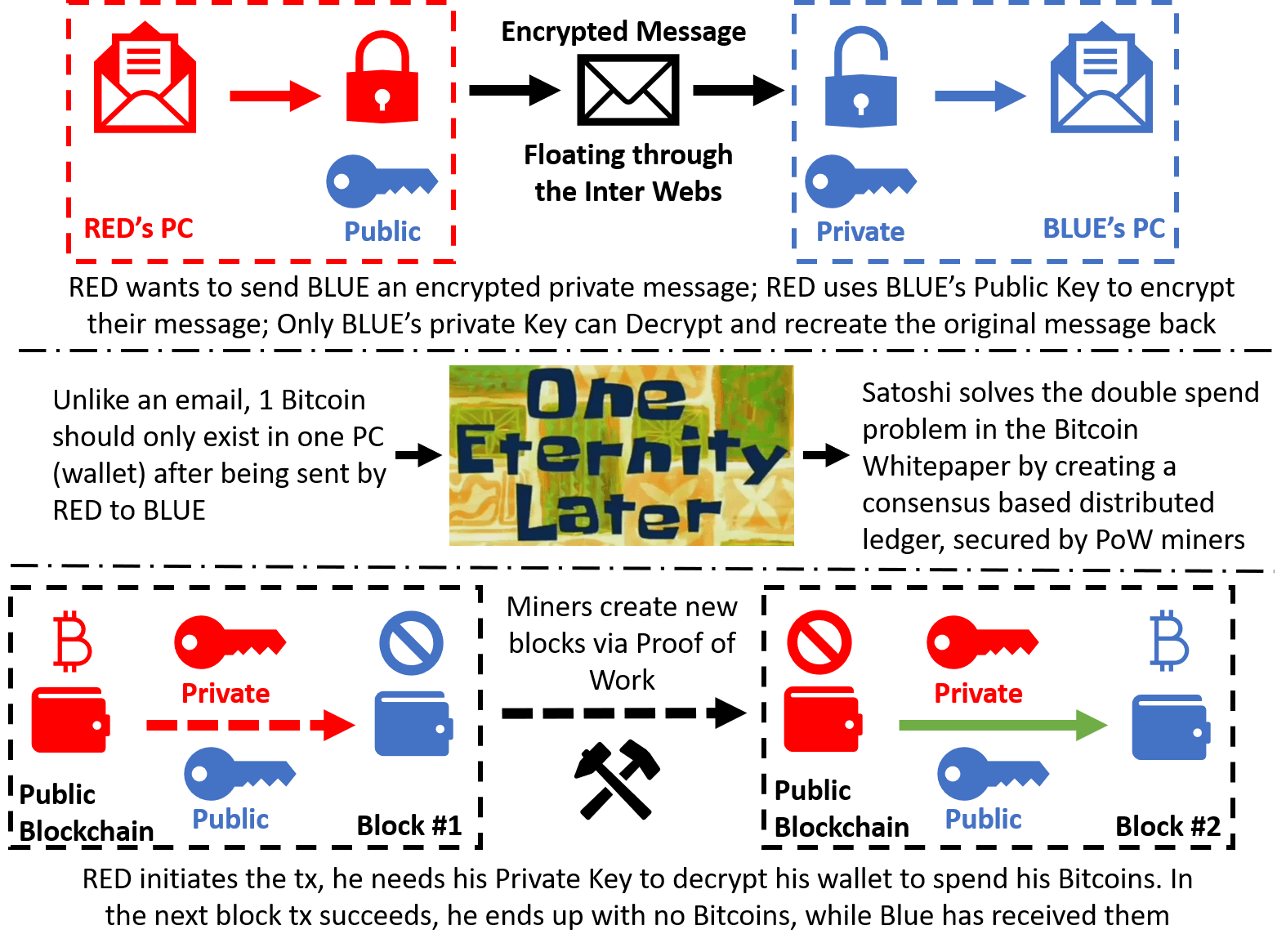
**Bitcoin and Cryptocurrencies – An example of applied Asymmetric Encryption: ** If you understand all the salient points of Asymmetric Encryption, then Bitcoin [3] (and most other blockchains) can be understood as simply a distributed form of public key/private key pairs. Once again for the practical implementation details, I will refer you to the authors who created the Bitcoin network architecture and consensus algorithm, and explained it in the Bitcoin Whitepaper: https://bitcoin.org/bitcoin.pdf
N.B.: If you are even remotely interested in working in Web 3, and/or investing in Crypto and NFTs, you need to do yourself a big favor to read and understand the Bitcoin whitepaper in whole. Read it a few times and understand it in full. This is seminal work, and will be remembered as such for ages to come. You need to know exactly what it says technically. A full history of the work leading up to Bitcoin’s creation is available here [4]: bitcointalk.org/index.php?topic=5290162.0
Private Keys (Spending Password), Public Keys, Addresses, Wallets: When you create a new wallet, a cryptographically secure pseudorandom number generator (CSPRNG) creates for you a pair of Private Key and Public Key.
The Public Key is derived by a one-way Hash of the Private Key. An address is derived by a one-way Hash of a Public Key, compressing and making it shorter in the process, and thus easier to use [5]. Digitize the address by saving it to a cloud backup service. Share it. Email it. Tweet it. It doesn’t matter, and the contents of the wallet cannot be compromised just because the address is shared or digitized.
The private key or spending key on the other hand is a totally different beast. The knowledge of the private key allows for the complete control of the assets within a wallet. A private key needs to be treated with the highest secrecy.
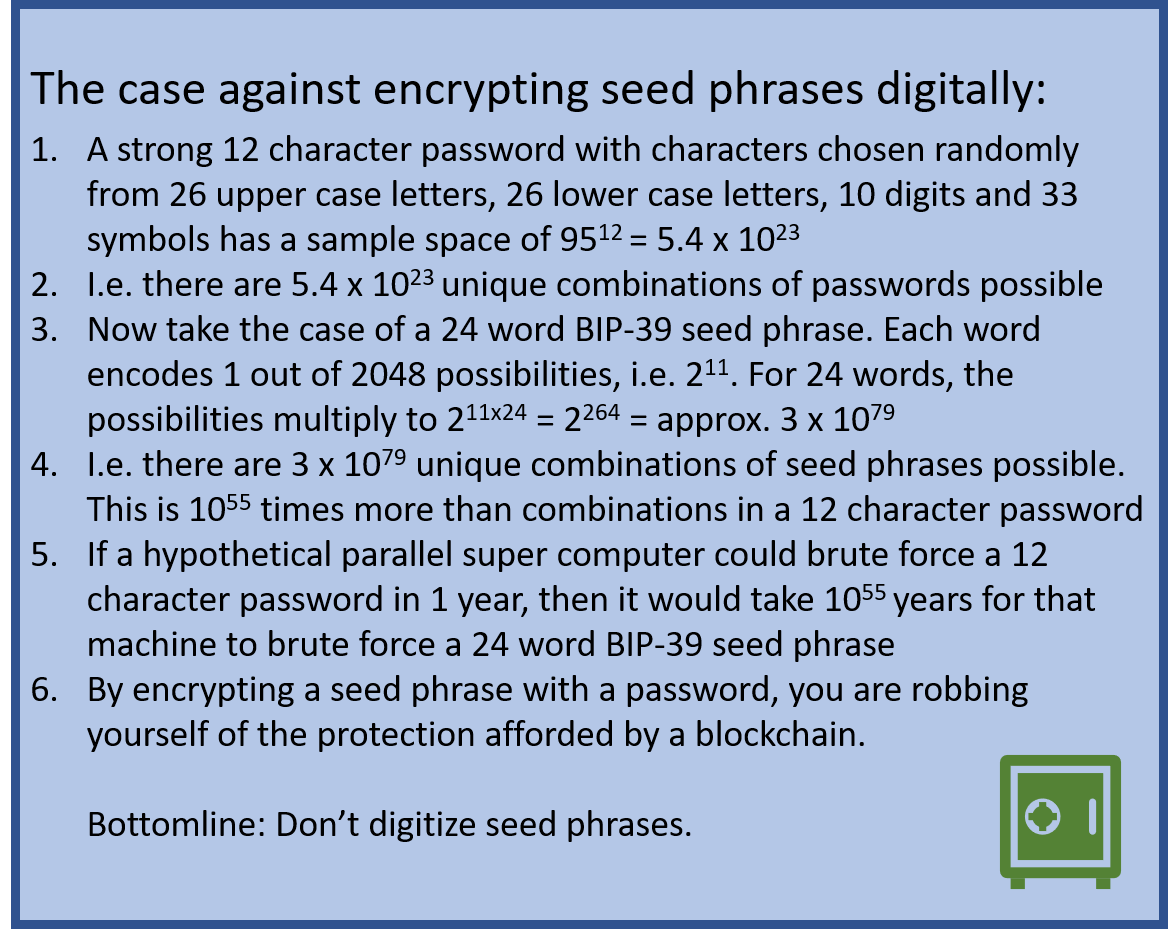
N.B.: To be technically specific, when creating any type of wallet, you will be shown a “seed phrase” that is 12 words (or 15 words, or 24 words) long. These words are randomly selected from a known and fixed dictionary of 2048 English words, called the BIP-39 (Bitcoin Improvement Proposal - #39) [6] word list. Knowledge of the seed phrase allows for the “private key or spending password” to be regenerated, and thus wallet control to be restored by the holder of the seed phrase.
Critically Important: The seed phrase should not be digitized, either as clear text or as a photograph. This means never saving it to cloud services like Google Docs, Microsoft OneDrive, Apple iCloud, Whatsapp, iMessage or any other type of cloud service. If you save it in clear text (even if it is a digital image), you will 100% lose your wallet contents. All images are scrubbed by Machine Learning algorithms to generate metadata, and thus a seed phrase will be easily found out and stick out like a sore thumb, waiting for the first human to spot it to remotely take control of the wallet. It is not a matter of “if”, it is a matter of “when”. Even if you encrypt the seed phrase to store it online, the encryption will likely be poor and will be easily brute forced. Remember, the seed phrase itself is enabling the State of the Art level of encryption; You only need to keep the seed phrase private and also secure it from loss to fire/water damage.
DO NOT DIGITIZE YOUR SEED PHRASE.
The only method to store a private key is to "write down" the seed phrase offline, i.e., physically in a notebook using pen and paper. The recommendation is to augment this, by additionally using a product like CryptoSteel [7] (https://cryptosteel.com/). This allows you to use alphabetical letters etched in stainless steel to be custom arranged in a series to constitute the words of the seed phrase. Cryptosteel ensures that a mishap like a fire or water damage will not destroy your seed phrase stored on paper. This is not a trivial point, there are thousands of people from the early days of crypto, who have lost/forgotten/thrown away their Bitcoin wallet seed phrase, and are locked out from their assets; in many cases these assets amount to 100s of BTC - a cool $2,000,000 at current prices.
References:
Wikipedia Contributors (2019). Public-key cryptography. [online] Wikipedia. Available at: en.wikipedia.org/wiki/Public-key_cryptography [Accessed 27 Jun. 2022].
Mehta, M. (2020). What Is Asymmetric Encryption & How Does It Work? [online] InfoSec Insights. Available at: sectigostore.com/blog/what-is-asymmetric-en.. [Accessed 28 Jun. 2022].
Nakamoto, S. (2008). Bitcoin: a Peer-to-Peer Electronic Cash System. [online] bitcoin.org. Available at: bitcoin.org/bitcoin.pdf [Accessed 27 Jun. 2022].
Held, D. (2020). Bitcoin Prehistory Tree. [online] bitcointalk.org. Available at: bitcointalk.org/index.php?topic=5290162.0 [Accessed 2 Jul. 2022].
Antonopoulos, A. (2014). 4. Keys, Addresses, Wallets - Mastering Bitcoin [Book]. [online] oreilly.com. Available at: oreilly.com/library/view/mastering-bitcoin/.. [Accessed 8 Jul. 2022].
Palatinus, M., Rusnak, P., Voisine, A. and Bowe, S. (2013). bips/bip-0039.mediawiki at master · bitcoin/bips. [online] GitHub. Available at: github.com/bitcoin/bips/blob/master/bip-003.. [Accessed 27 Jun. 2022].
Cryptosteel. (n.d.). Cryptosteel - The Mother of All Backups. [online] Available at: cryptosteel.com [Accessed 27 Jun. 2022].
The author holds a M.S. in Engineering from Columbia University, and has a decade of research and industry experience in software and hardware design. He has been researching crypto security since early 2021. He can be followed on Twitter: @MetaversityOne and his Hashnode Blog: https://cryptosecurity.hashnode.dev/
This work was made possible due to the financial assistance by Developer DAO, Treasure DAO/Smol Ecosystem and vVv Fund, which covered in part the costs of developing this research series. The author is greatful to these organizations for their support.