Security in Crypto, Hardware Wallets and Pseudonymity - Part 1/7
Part 1 discusses a series of introductory topics such as passwords, 2 Factor Authentication (2-FA) methods, their comparison and best practices.
**Part 1 discusses a series of introductory topics such as passwords, 2 Factor Authentication (2-FA) methods, their comparison and best practices. **
The first rule of crypto is: since cryptocurrencies and NFTs are digital assets, and they can be stolen digitally (which is a very smooth, silent and low risk operation for a skilled scammer/hacker, especially when coupled with social engineering). The very first rule as a crypto/NFT holder is “Don’t talk about your net worth in crypto to anyone.”
Since there are myriad methods of hacks and scams, and as a non-cybersecurity expert, you will most likely be unable to keep up with the fast-evolving pace of scams and hacks, revealing your crypto net worth puts an “number on your head” for a scammer/hacker to target. Given a sufficiently high value, this becomes the reward for which one or more hackers may then try to target you.
So, the rule number one, is never say out loud, type in a Twitter thread or Discord channel a $ value of your holdings. And as much as possible, keep your real name and address off all social media channels. The second part is important, because if a real-life name and address can be tied to your wallet addresses, the open nature of the blockchain puts you at a risk of being targeted.
The following parts of this series will cover different aspects about wallets (hot wallets, hardware wallets, etc.) and private keys. We will cover a bunch of introductory topics before we move on to wallets and private keys. Having thorough working knowledge of the introductory topics, will help make it a breeze to actually use the hardware wallet. The actual usage will be covered in a follow up series.
Passwords and 2-FA: Take the case of passwords. It is commonly accepted that “easily guessable passwords” with low degree of randomness, and password reuse across websites is the number one reason for a victim losing big when a single password of theirs is compromised. This is because when passwords are compromised they are routinely sold to other scammers. Thus if you reuse the same password everywhere, credentials of a single account of yours being hacked, allows scammers to get into all of your accounts across platforms such as email/socials/exchange accounts.
A secondary fail safe is the use of 2-FA, such as Google Authenticator/Twilio Authy. 2-FA creates an extra layer of protection beyond passwords and can take various forms such as something you know (e.g. a PIN), something you have (e.g. a security key), or something you are (e.g. biometric patterns) [1]. It is important to use 2-FA for every account on every type of platform - including email, crypto exchange accounts, and social media accounts (Twitter, Discord, Telegram, etc).

**Google Authenticator/Twilio Authy based 2-FA preferred over SMS based 2-FA: ** It has been seen that phone number/SMS based 2-FA are easily hacked by scammers, by using the loopholes in mobile phone provider systems, such as reissuing a sim card to an impostor without doing a full verification of the person authenticating them as the original customer, also known as the SIM swap scam [2,3]. As noted in the referenced articles, SIM Swap Scams have exploded in the 2020-22 period, and thus you must take necessary precautions to not fall for this and become a statistic.
Hence, the recommendation is to always use 2-FA and always use the Google Authenticator/Twilio Authy based 2-FA. These apps can be downloaded from the App Store for iOS and Play Store for Android devices.
Comparing Google Authenticator with Twilio Authy: Keep in mind that a Google Authenticator account is not tied to a phone number, and does not have a cloud based restore option. On the other hand, Twilio Authy accounts are tied to a phone number mandatorily by design and backup all the 2-FA tokens to the cloud. This makes it easy to restore all your 2-FA accounts to a new phone/across devices, in case you damage or lose your current phone. But keep in mind that once again if you fall victim to SIM swap scam, someone can restore and steal your Twilio Authy based 2-FA tokens remotely via a restore from the backup on the cloud. You must turn off the multi-device option by going to Settings (gear symbol) -> Devices -> Turn “Allow Multi-device” OFF [4].
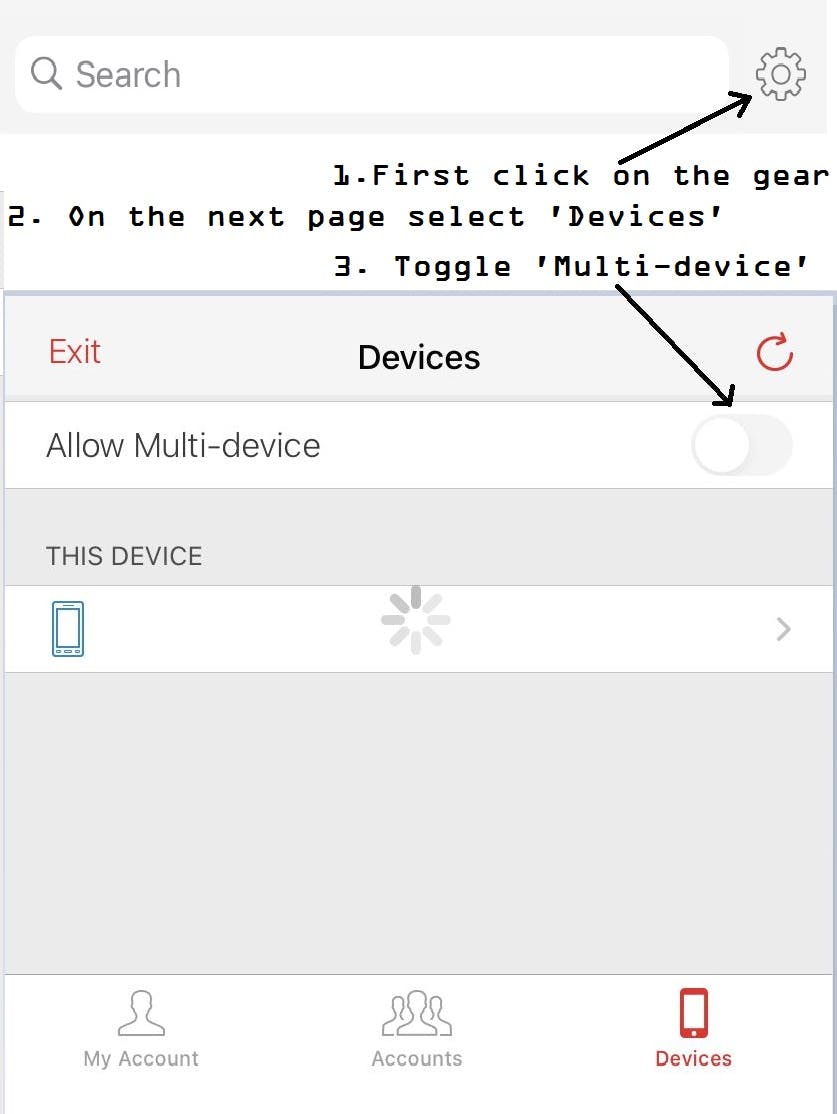
A related idea is to sync/restore Twilio Authy to an additional device of yours in advance (before you need the backup), and then to turn OFF the “Allow Multi-device”. This means no newer devices can restore your Authy account, but at the same time you have a physical device in your possession that is already synced to your Authy account.
References:
Twilio Authy (2016). Authy. [online] Authy. Available at: authy.com/what-is-2fa [Accessed 11 Jul. 2022].
Norton U.S.. (n.d.). SIM swap fraud explained and how to help protect yourself. [online] Available at: us.norton.com/internetsecurity-mobile-sim-s.. [Accessed 27 Jun. 2022].
Wikipedia Contributors. (2021). SIM swap scam. [online] Available at: en.wikipedia.org/wiki/SIM_swap_scam [Accessed 27 Jun. 2022].
Twilio Authy Help Center. (n.d.). Enable Or Disable Authy Multi Device. [online] Available at: support.authy.com/hc/en-us/articles/3600163.. [Accessed 27 Jun. 2022].
The author holds a M.S. in Engineering from Columbia University, and has a decade of research and industry experience in software and hardware design. He has been researching crypto security since early 2021. He can be followed on Twitter: @MetaversityOne and his Hashnode Blog: https://cryptosecurity.hashnode.dev/
This work was made possible due to the financial assistance by Developer DAO, Treasure DAO/Smol Ecosystem and vVv Fund, which covered in part the costs of developing this research series. The author is greatful to these organizations for their support.
